Group 7 Members
David Lackey
Conducted an hour and a half of observations. Led the blogging / project managed.
John O’Neill
Conducted an hour of observations and thirty minutes of interviews. Led user-casing / user tasking.
Horia Radoi
Conducted 40 minutes of observations and interviews and was the primary story-boarder.
Overview
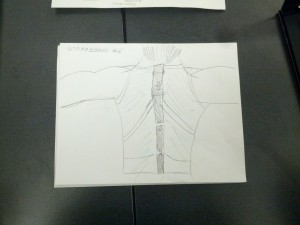
The problem that we are addressing is bad sitting posture with students who are working at desks. Our proposed solution is a wearable posture detector in the form of an under armor shirt. This solution addresses the problem because we can gather all of the necessary information about the user’s back posture and alert them through the device that they’re wearing. It can be easily embedded in the user experience without taking too much away from the task at hand.
Description of Observations
Our target user group includes people who study at desks and who are concerned with their sitting posture. Additionally, these people need to be comfortable with the idea of technology helping their well-being. We could have focused on posture in other realms, such as weight-lifting, etc, but we wanted to focus on an application of posture where many people spend a great deal of time. Also, back problems associated with sedentary life styles is quite common.
See Appendix for thorough collection of observations.
User 1
User number 1 is a female undergraduate who has a history of back-related problems and has to spend a majority of their day in front of a laptop. They often enjoy using their computer for non-work activities, including watching videos, but dislike how using a laptop often requires you to look down / crane your neck. One of their greatest priorities is being able to focus in on their laptop work for hours at a time. They are a great candidate, given their applicability to our target user group (undergraduates who work at desks,) their history of dealing with back issues, and their laptop-heavy workflow.
User 2
We were unable to conduct an interview with user 2, but, based on the hour and fifteen minutes that we observed her for, we were able to extract a lot of important information about long-term seating habits for a relevant target user.
She was studying scientific books in the Friend Engineering Center Library, meaning that it is very likely that she is some sort of engineering student.
User 3
Our third user does not study in libraries that often. She does, however, study in a chair at a desk in her room. Without the scrutiny of others, it’s harder for her to force herself to not slouch. Her priorities include making her room a productive, but healthy place to study. She likes to study in her room more than the library.
Observations
To observe people, we would sit towards the edges of large seating areas in libraries. This allowed us to pinpoint students who seemed to be a part of the target user group. We identified these students by their noticeably bad seating posture.
Each of our users were clearly dealing with discomfort from long periods of sitting. To deal with it, they would often stretch their backs, change to another position, or rub their necks. See the Appendix A for the minute by minute observations of user 2. Many of the observed mannerisms (such as those discussed in the above paragraph) were present in our observations of other users as well.
We found user 3’s note about the scrutiny of others to be very interesting. Being scrutinized by others actually has an impact on your posture. Being able to impose this scrutiny artificially through the device could prove to be beneficial.
A unique thing about user 1 is that she had back problems earlier in life, so back posture is especially important.
In terms of workflow, users 1 and 2 both appreciated long periods of time to focus on work. User 3, however, approached work with a more off and on approach. User 3 said that this made it a little easier to maintain proper back posture, since it was for shorter periods of time.
Task Analysis
- Who is going to use the system?
Undergraduate students who are concerned with their back posture while working and wish to improve it through the use of technology. Can be adapted to fit general people who are concerned about their posture while doing office work, or people who need a specific form for an athletic activity.
- What tasks do they now perform?
Working at desks with improper back, neck, and wrist posture, often for extended periods of time (over 15 minutes in a single posture). This causes problems in the long run. A specific target group would be young adults, who are at the end of their growth period, and for whom a poor posture can have long-lasting health effects.
- What tasks are desired?
To maintain proper posture while working at a desk.
- How are the tasks learned?
An extremely basic, printed walkthrough will accompany the hardware. This manual will explain how a user sets a “default” / “base” posture, and what will happen when one deviates from the base posture. At the same time, a doctor can set up a desired position during a consultation, and the user will have the choice to move between his personal mode or the doctor suggestion.
- Where are the tasks performed?
Wherever a student is working at a desk (the library, their room, etc.) or doing an activity that would put the back in a non-ideal position.
- What’s the relationship between user & data?
The user can interact with the data and set up an ideal back position, can switch between two modes (one of which is considered to be a physician’s recommendation). The analysis and alerting will be done automatically.
- What other tools does the user have?
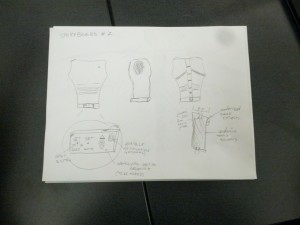
None. He will interact with the computer through SET and CHANGE buttons, and will need to wear the hardware in order for it to function.
- How do users communicate with each other?
They don’t. This is an individual product. Different modes can be loaded using the USB cable.
- How often are the tasks performed?
It is recommended for users to wear the device every time their back will be in the same position for a long period of time (ie. while working, doing homework, working out etc.)
- What are the time constraints on the tasks?
There will be no time constraints except for the battery life of the device.
- What happens when things go wrong?
If things go wrong, the system may be encouraging bad back habits, which is counterproductive.
Description of Three Tasks
Task #1: Set up a desired back position.
The user must designate the “default” or “base” posture that will function as the user’s desired posture. This can be done by the user (or, for use cases outside of those we are studying, by a medical professional.) The user chooses a good posture and presses a button on the device to set the base;
the system will memorize this ideal position in order to record how far away the user deviates from it.
Difficulty Analysis
Finding a desirable posture requires no hardware or software – just an acute attention to how your body is feeling when undergoing certain postures. This means that our task is easy when performed using pre-existing tools and applications. Under a system, however, a “desired back position” has a specific definition and requires calibration, thus the level of difficulty is moderate.
Task #2: Alert user if back position / posture deviates too far from desired posture. Small motors in the system (ideally along the back / along the area of bad posture) will vibrate to notify the user that they have bad posture. We need to test whether we notify the user after a certain threshold of deviance (slouches too much,) if an improper posture is held for too long a duration (slouching for too long,) or some combination of the two.
Difficulty Analysis
One can currently ask another person to monitor their own posture, but this requires an additional person who is watching at all times, making this difficulty-level moderate. However, the device alerts the user automatically / without volition of the user, making this task difficulty easy.
Task #3: Monitor how their posture changes. User can optionally plug the wearable device into the laptop, which will record the readings of the resistors. We can use this data to show the users – in a nice, visual format – how often and how much they deviated from their ideal posture.
Difficulty Analysis
There may be some medical device that quantifies / provides feedback on a patient’s posture, but we are unaware of such things. This high barrier is why we are monitor this task as difficult. However, with this device, the user only needs to plug in the device, which is why we label this task as moderate.
Interface Design
Description
The system is a wearable device that helps users maintain good posture. It monitors the user’s back posture and alerts them when it deviates from a desirable position, and can optionally provide the user with data on when and by how much they deviate from their desired posture. In form, the device is similar to underarmor; this is because the slim fit allows the sensor to more accurately monitor changes in the user’s posture. If the user has a chance to plug the device into a laptop, a program can extract readings from the device, allow the user to view changes in their posture over time. Ideally, such a system would encourage healthier habits in regards to posture. To our knowledge, there is currently no wearable system is dynamically monitors and provides feedback for bad posture.
Storyboards


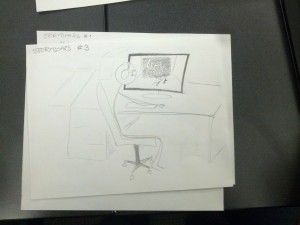


System Sketches
Appendix A – Minute by Minute Observations of User 2
- Where: Friend Library 2nd Floor
- When: 12:00 PM on 3/8/12
- Girl in green jacket sits and gets comfortable
- Puts jacket around chair
- Has a small world coffee
- First sits on edge of her seat and uses smartphone
- Stands up and starts to pull items out of backpack
- Pulls out Windows computer
- Sits back down and rolls back sleeves
- Ties back hair
- Cleans glasses
- Looks out the window
- Immediate posture
- Edge of seat
- One foot on ground
- Kind of hunched over computer
- Gets up and takes a photo of the snow with smartphone through window
- Sits back down
- Feet all over the place
- Upper body pretty steady
- Both elbows out resting on the table
- Head forward over keyboard
- Shoulders close together
- After 5 mins, sits up tall briefly
- Adjusts hair and maintains position for a few seconds
- Returns to a position with a lesser posture
- Head is more forward and lower
- More slumped over computer in general
- Slowly gravitates to original position over the course of several minutes
- When: 12:15 PM
- Legs reach a somewhat consistent form of being crossed
- Head gets lower again
- When: 12:21
- Rubs neck with left hand
- Rolls up sleeves and returns to work
- Reaches the new posture
- Elbows still resting on table
- Left hand on neck
- Right hand using computer
- Puts on big green jacket
- Goes to original posture
- When: 12:40
- Hunched more forward
- Hunches over her phone every once in a while to send a text
- When: 12:45
- Leans more on right side
- Sits up tall and puts elbows close together as a stretch
- Almost back to original posture, elbows slightly more in
- Elbows out again, more slump
- Leans way forward with arms on lap and stays with this new posture
- Leans back in chair after brief back twist stretch
- Leans forward again
- Gets up and throws coffee away
- When: 12:50
- Arms on lap, hunched forward
- leaning forward on right arm
- Sits tall and scoots chair forward so that her back is flush to the back of the chair and she’s close to desk
- When: 1:00
- Left elbow on chair’s left arm
- Leans
- When: 1:10
- Shift from elbow to elbow on chair’s arms
- Looks uncomfortable
- When 1:15
- Stretches back backwards over chair
- Leans forwards again with arms on lap